Heartbleed Bug Explained
We take this explanation fromhttp://www.theregister.co.uk/2014/04/09/heartbleed_explained/and summarize it ourselves.
The Heartbeat is a way to maintain SSL session persistence.
The bug is contained in the SSL3 heartbeat message.
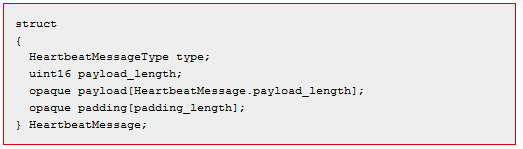
The graphic below shows the c-language code for the Heartbeat message in the OpenSSL source code.
In this data structure, the length of the message is given as payload_length.
This is the SSL record structure, from the SSL standard.
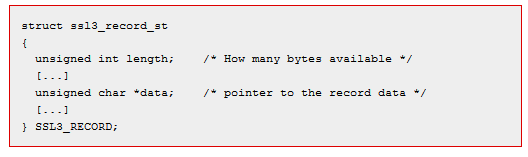
It shows the length as well.
But the OpenSSL code reads the length as payload length from the OpenSSL structure and not the SSL3 structure.
In the sample below the area shaded in red is data beyond the length of the TLS1_HB_REQUEST.
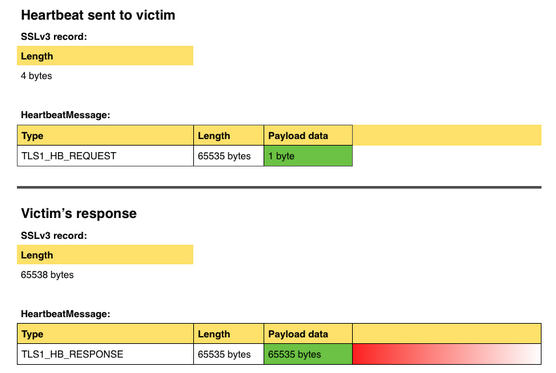
That, of course, gives the program access to memory outside the OpenSSL heartbeat message.
What Does this Mean?
If someone obtained the session keys, they could use these to replay one user session and decrypt that.
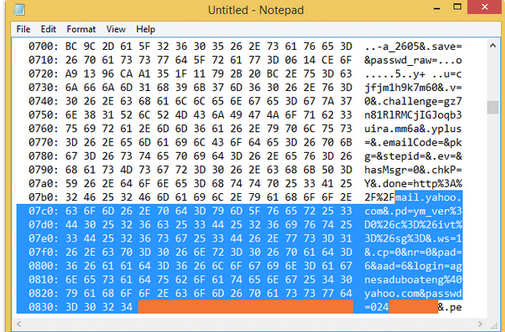
This would be difficult to do in real time.
If someone obtained passwords it is obvious what this means.
Who does it affect?
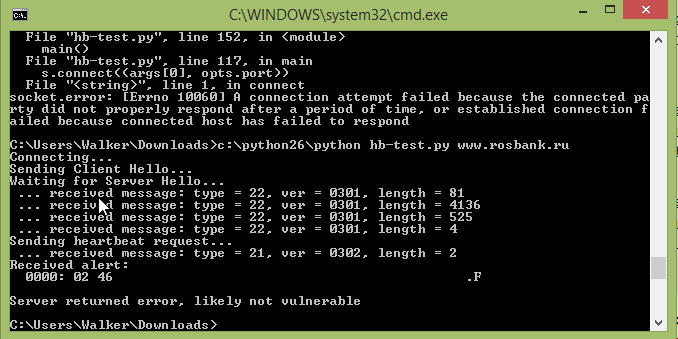
We discuss this below.
Apache Mod_ssl
The Apache module mod_ssl uses OpenSSL to for SSL.
The current version of the Apache windows binary (2.2.22) that includes mod_ssl is from 30 January 2014.
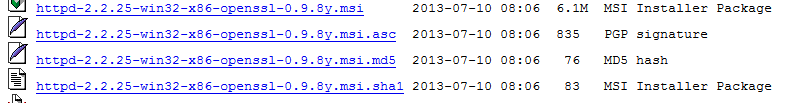
As it’s possible for you to see it uses OpenSSL 0.9 which is from 10 May 2012.
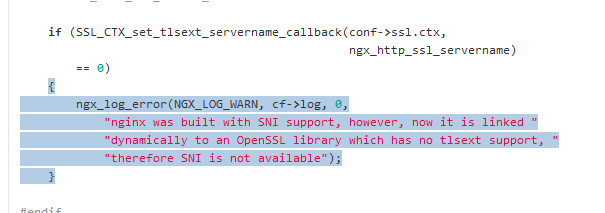
This is true for Windows and Linux.
Just download the latest version of OpenSSL.
How do I know if my OS is affected?
prior to OpenSSL 1.0] and (b) you have not patched it.
For example, Ubuntu 12.04.4 says it uses open SSL 1.0.1.
So it has the version of OpenSSL with the bug.
Your users should change all their passwords too, but you do not need to tell them that.
They probably have already read about it in the news.
Presumably these do not use the Heartbeat module needed to maintain persistence with a user.
But that would warrant further investigation.