Documents leaked by Edward Snowden say they have not been able to do it.
The US government uses Tor itself when its employees travel overseas.
The source and destination IP addresses remain visible.
This means someone intercepting this traffic can read from where it is going and from where it is sent.
If you are Edward Snowden talking to The Guardian newspaper, your privacy could be compromised.
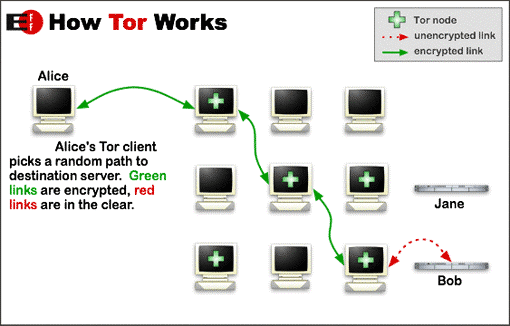
Courtesy of www.torproject.org
Tor works by encrypting the destination IP address.
So, someone could not tell where the data came from, even if they could defeat the encryption.
It does not know where the data is coming from.
There are thousands of Tor relays in operation.
When Tor sends data, it randomly picks which relay to use to receive the next hop.
That relay then picks the next relay and so on.
For a spy, whose driver is captured, that could be a bad thing.
The exit point has the same issue.
You cannot send email to an SMTP server that does not support TLS: not many do.
But there are websites that are configured to handle encrypted traffic from Tor.
These are called hidden services.
What about the actual RSA encryption algorithm used to encrypt the data?
That can take years, if the encryption key is large enough.
Tor uses SOCKS, which means a proxy server.
This way you do not need to configure your web client to use Tor.
To summarize, Tor is a useful tool for those who need something more secure than VPN.