The malicious actions were very similar to RuMMS campaign which was aimed at the Russian segment.
Unlike RuMMS, described in 3 campaigns which were using the users screen spoofing technique.
After contact with the system Trojan scans the victims unit, and monitors the applications running in the background.
Thus the user is prompted for credentials in the form, controlled by the hackers.
However, malicious activity is not stopped in May.
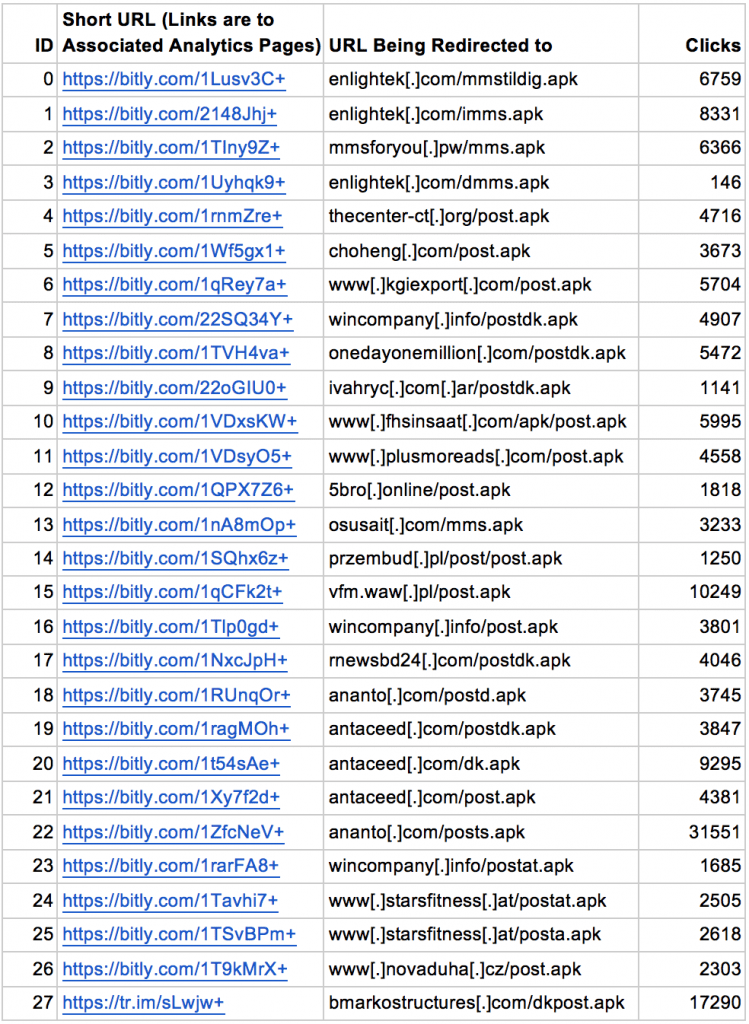
Unlike RuMMS, the current campaign is not only using the free hosting to host malware.

As the attackers register domain names, use a shortened Bit.ly link service and compromised websites.
FireEye Security Experts found 12 C & C servers hosted in 5 countries.
In addition, the 4 C & C servers are located on a subnet 85.93.5.0/24.

This indicates the presence of control over the connection resources on the connection segment.
